Introduction
This post solves the mystery of Donny's System and outlines how to utilize memory forensics methodology to uncover artifacts from memory dumps
Tools: Volatility, Yara & Windows Powershell
Analysis
Six-step investigative methodology by SANS
Run Volatility pslist plugin to see active running processes
PS C:\volatility> .\vol.exe -f .\unknown.vmem --profile=WinXPSP3x86 pslist
Just to remind that all process creation and termination timings are specified in UTC. Ensure to change them to system timezone while correlating the events with other sources of evidence
game.exe clearly looks suspicious as it ran and exit in a short span of time. The most interesting part was explorer.exe spawned number of system commands.
Observe the creation time of processes followed by game.exe process
PS C:\volatility> .\vol.exe -f .\unknown.vmem --profile=WinXPSP3x86 pslist | Select-String '1716'
Run Volatility dlllist plugin to identify the path from where it was executed and dlls loaded by game.exe, but the process was terminated and unable to read PEB
PS C:\volatility> .\vol.exe -f .\unknown.vmem --profile=WinXPSP3x86 dlllist -p 1044
Run Volatility connections plugin to identify any active connections
PS C:\volatility> .\vol.exe -f .\unknown.vmem --profile=WinXPSP3x86 connections
Suspicious game.exe PID 1044 established an active connection with remote host 192.168.78.128 on port 4444. A quick search for port 4444 on google indicates that port 4444 deals with metasploit framework ( Assuming the analyst doesn't have knowledge of metasploit)
It's been understood that meterpreter reverse shell uses port 4444 as by default for any incoming connections
To Confirm that game.exe process is a backdoor (created by msfvenom)which established connection back to the attacker's host, Run Volatility malfind Plugin to identify any sort of code injection.
Meterpreter uses Reflective DLL injection mechanism to inject DLL into legitimate victim process.
PS C:\volatility> .\vol.exe -f .\unknown.vmem --profile=WinXPSP3x86 malfind
The legitimate explorer.exe PID 1716 process was injected with an executable DLL, observe the PAGE_ EXECUTE_READWRITE permissions, VADS represents that there is no memory mapped file before at address space 0x3600000
Run Volatility malfind again to dump all memory injected regions.
PS C:\volatility> .\vol.exe -f .\unknown.vmem --profile=WinXPSP3x86 malfind -D .\malfind\
Upload those malfind dumped files to Virustotal for a quick analysis
It's clear that meterpreter stage was injected into explorer.exe and any command performed through meterpreter session was disguised as legitimate explorer.exe process
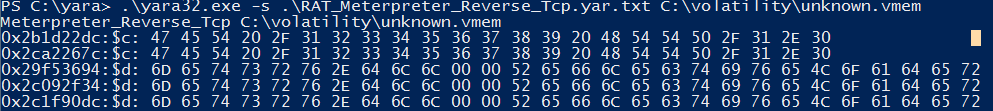
Meanwhile running a quick yara rule identified the memory dump as an opened meterpreter reverse shell to attacker's system
Run strings.exe on malfind dumped files to find meterpreter metsrv.dll stage 1 and meterpreter extension dlls stdapi and priv
Look for meterpreter extension DLL priv
Recommended to read about stage and stageless meterpreter payloads
Run Volatility userassist to find the executable which were run by Donny last time
PS C:\volatility> .\vol.exe -f .\unknown.vmem --profile=WinXPSP3x86 userassist | Select-String 'game.exe' -Context 1,3
Note: Process creation time is in UTC
This post solves the mystery of Donny's System and outlines how to utilize memory forensics methodology to uncover artifacts from memory dumps
Tools: Volatility, Yara & Windows Powershell
Analysis
Six-step investigative methodology by SANS
- Identify rogue processes
- Analyze process DLLs and handles
- Review network artifacts
- Look for evidence of code injection
- Check for signs of rootkit
- Dump suspicious processes and drivers
Run volatility imageinfo plugin to identify profile
PS C:\volatility> .\vol.exe -f .\unknown.vmem imageinfo
Run Volatility pslist plugin to see active running processes
PS C:\volatility> .\vol.exe -f .\unknown.vmem --profile=WinXPSP3x86 pslist
Just to remind that all process creation and termination timings are specified in UTC. Ensure to change them to system timezone while correlating the events with other sources of evidence
game.exe clearly looks suspicious as it ran and exit in a short span of time. The most interesting part was explorer.exe spawned number of system commands.
Observe the creation time of processes followed by game.exe process
PS C:\volatility> .\vol.exe -f .\unknown.vmem --profile=WinXPSP3x86 pslist | Select-String '1716'
Run Volatility dlllist plugin to identify the path from where it was executed and dlls loaded by game.exe, but the process was terminated and unable to read PEB
PS C:\volatility> .\vol.exe -f .\unknown.vmem --profile=WinXPSP3x86 dlllist -p 1044
Run Volatility connections plugin to identify any active connections
PS C:\volatility> .\vol.exe -f .\unknown.vmem --profile=WinXPSP3x86 connections
Suspicious game.exe PID 1044 established an active connection with remote host 192.168.78.128 on port 4444. A quick search for port 4444 on google indicates that port 4444 deals with metasploit framework ( Assuming the analyst doesn't have knowledge of metasploit)
It's been understood that meterpreter reverse shell uses port 4444 as by default for any incoming connections
To Confirm that game.exe process is a backdoor (created by msfvenom)which established connection back to the attacker's host, Run Volatility malfind Plugin to identify any sort of code injection.
Meterpreter uses Reflective DLL injection mechanism to inject DLL into legitimate victim process.
PS C:\volatility> .\vol.exe -f .\unknown.vmem --profile=WinXPSP3x86 malfind
The legitimate explorer.exe PID 1716 process was injected with an executable DLL, observe the PAGE_ EXECUTE_READWRITE permissions, VADS represents that there is no memory mapped file before at address space 0x3600000
Run Volatility malfind again to dump all memory injected regions.
PS C:\volatility> .\vol.exe -f .\unknown.vmem --profile=WinXPSP3x86 malfind -D .\malfind\
Upload those malfind dumped files to Virustotal for a quick analysis
It's clear that meterpreter stage was injected into explorer.exe and any command performed through meterpreter session was disguised as legitimate explorer.exe process
Meanwhile running a quick yara rule identified the memory dump as an opened meterpreter reverse shell to attacker's system
Look for meterpreter extension DLL priv
Recommended to read about stage and stageless meterpreter payloads
Run Volatility userassist to find the executable which were run by Donny last time
PS C:\volatility> .\vol.exe -f .\unknown.vmem --profile=WinXPSP3x86 userassist | Select-String 'game.exe' -Context 1,3
Note: Process creation time is in UTC



















Comments
Post a Comment